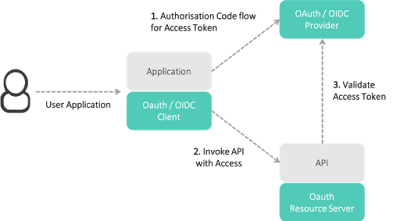
OpenID Connect (OIDC) is an authentication layer on top of OAuth 2.0, an authorization framework.[1] The standard is controlled by the OpenID Foundation.
- Authorization Code Flow
- Implicit Flow
- Resource Owner Password Credentials Flow
- Client Credentials Flow
- Refresh Token Flow
A way for a client to obtain an access token on behalf of a user via a REST invocation.
curl --location --request POST 'http://localhost:8180/auth/realms/spring2/protocol/openid-connect/token' \
{
- "issuer": "http://localhost:8180/auth/realms/spring2",
- "authorization_endpoint": "http://localhost:8180/auth/realms/spring2/protocol/openid-connect/auth",
- "token_endpoint": "http://localhost:8180/auth/realms/spring2/protocol/openid-connect/token",
- "introspection_endpoint": "http://localhost:8180/auth/realms/spring2/protocol/openid-connect/token/introspect",
- "userinfo_endpoint": "http://localhost:8180/auth/realms/spring2/protocol/openid-connect/userinfo",
- "end_session_endpoint": "http://localhost:8180/auth/realms/spring2/protocol/openid-connect/logout",
- "jwks_uri": "http://localhost:8180/auth/realms/spring2/protocol/openid-connect/certs",
- "check_session_iframe": "http://localhost:8180/auth/realms/spring2/protocol/openid-connect/login-status-iframe.html",
- "grant_types_supported": [
- "authorization_code",
- "implicit",
- "refresh_token",
- "password",
- "client_credentials"
- "response_types_supported": [
- "code",
- "none",
- "id_token",
- "token",
- "id_token token",
- "code id_token",
- "code token",
- "code id_token token" .....
Refresh token:
curl -X POST \
http://localhost:8180/auth/realms/spring2/protocol/openid-connect/token \
-H 'Content-Type: application/x-www-form-urlencoded' \
-d 'grant_type=refresh_token&client_id=login-app2&client_secret=welcome1&refresh_token=eyJhbGciOiJIUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICJhZTY0YTA1Mi1iMGJlLTRjY2UtODUxNS1lYTM0MDY5YWQ1YTMifQ.eyJleHAiOjE2MTE5NTI3MjYsImlhdCI6MTYxMTk1MDkyNiwianRpIjoiZjA4MjFhMGMtZjdmNi00YmRkLTg4YTctZmZkOTIwZTA0YWQ5IiwiaXNzIjoiaHR0cDovL2xvY2FsaG9zdDo4MTgwL2F1dGgvcmVhbG1zL3NwcmluZzIiLCJhdWQiOiJodHRwOi8vbG9jYWxob3N0OjgxODAvYXV0aC9yZWFsbXMvc3ByaW5nMiIsInN1YiI6ImRkNGU2ZTQ2LWIwMjQtNDZmYS05ZjUzLWM3OWE2MDM5YWIzZiIsInR5cCI6IlJlZnJlc2giLCJhenAiOiJsb2dpbi1hcHAyIiwic2Vzc2lvbl9zdGF0ZSI6IjUyYmU0ZTllLTVhNWMtNDFiZC1hZWVlLTg4ZjFiNTNhYjgwNiIsInNjb3BlIjoib3BlbmlkIGVtYWlsIHByb2ZpbGUifQ.FIAstcSWnq1ZUdHfgbIY9Z3u9_a2ywoFe9vxV-vwp6E'
Resources:
- https://en.wikipedia.org/wiki/OpenID_Connect
- https://medium.com/@darutk/diagrams-and-movies-of-all-the-oauth-2-0-flows-194f3c3ade85
- https://www.ubisecure.com/single-sign-on/single-page-application-and-openid-connect/
- https://www.manning.com/books/spring-security-in-action
- https://www.baeldung.com/spring-boot-keycloak
- https://api-university.com/openid-connect-cheat-sheet/
- https://backstage.forgerock.com/docs/am/6/oidc1-guide/
- https://medium.com/@robert.broeckelmann/openid-connect-authorization-code-flow-with-red-hat-sso-d141dde4ed3f
- https://auth0.com/docs/flows/authorization-code-flow
- https://medium.com/@robert.broeckelmann/refresh-token-support-in-oauth2-oidc-debugger-c792b3a3f65a
- https://github.com/rcbj/oauth2-oidc-debugger
- https://github.com/nbarbettini/oidc-debugger
Live here: https://oauthdebugger.com or https://oidcdebugger.com - https://medium.com/devops-dudes/securing-spring-boot-rest-apis-with-keycloak-1d760b2004e
- https://www.keycloak.org/docs/4.8/server_admin/
- https://auth0.com/docs/authorization/which-oauth-2-0-flow-should-i-use
- https://oauth.net/2/grant-types/implicit/
- https://www.javacodegeeks.com/2019/01/right-flow-job-oauth-2-0-flow-should-use.html
- https://auth0.com/docs/flows/call-your-api-using-resource-owner-password-flow
- https://curity.io/resources/tutorials/howtos/flows/refresh-tokens/
- https://www.authlete.com/developers/pkce/#4-pcke-token-request
- https://auth0.com/docs/flows/call-your-api-using-the-authorization-code-flow




No comments :
Post a Comment